
The most recent computer viruses have increased their ability to steal your sensitive data and damage your PC. Continue reading to learn more about them and take precautions in advance.
Do you think using your computer or the internet puts you in danger? Most people hold the same viewpoint. People now realize how crucial it is to protect their data from outside threats as cybercrime rates rise. Well, the problem of cybercrime is not new. It has been around for ages. However, the repercussions may now be even more serious. You can become a victim of cyberattacks at any time.
Additionally, attackers have access to any private information and are free to use it in whatever way they want, including plotting terrorist attacks. The only way to remain safe is to stay informed about the most recent computer viruses and prepare to remove them. Knowing about them will help you prepare your antivirus software to combat these harmful computer viruses.
Top 10 Latest Computer Viruses You Need to Protect Yourself From in 2023
Every year, numerous new and malicious viruses knock on our doors. If they gain access to your system, they have the potential to seriously harm it and compromise your data. So, here are some of the harmful and latest viruses that you should be aware of.
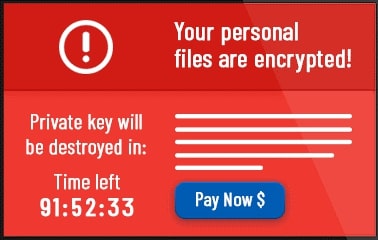
1. CryptoMix Clop Ransomware
CryptoMix Clop Ransomware is one of the most dangerous computer viruses that threaten not only the privacy of your personal information but also the information of other users connected to the same network. Yes, this strong ransomware targets the entire network rather than just one particular computer. The first thing this virus does is turn off any installed antivirus software on your computer.
In order to combat this dangerous virus, you should upgrade or replace any weak antivirus software. It’s not over yet. The virus also modifies the extensions of existing files on your computer and encrypts them. Clop or .Clop extension.
Following all of this, a note warning you of the attack and requesting a ransom is displayed. If they are unable to contact you, its authors also threaten to disable the security tools.
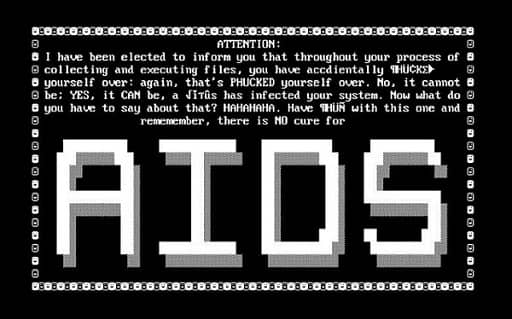
2. Cyborg Ransomware
Cyborg Ransomware is another dangerous computer virus and is frequently referred to by the term “AIDS” (Aids Info Disk Trojan). Floppy disks were thought to be a safer option in the past. However, this Trojan Horse rendered them extremely unsafe. Yes, this virus can enter your computer through the floppy disk you’re using and corrupt it. It replaces AUTOEXEC.BAT and keeps track of how many reboots the system undergoes in an effort to impede its functionality.
You should use more caution if you use Windows 10 because recently, fake Windows 10 software updates contained its new variant. Avoid clicking on any unknown attachments with “.jpg” extensions to protect yourself from this ransomware.
Also know: Best Internet Security Software for Windows PC in 2023
3. Trojan Glupteba
This is possibly one of the most well-known computer virus names ever. It gains access to the system using exploit kits or other malware. You won’t even be able to detect a virus infection on your computer once it has infected the system software. It communicates with your IP address and ports directly while posing as legitimate software in order to gather your private data.
In addition, it leads you to other risky and unidentified websites, including sportpics.xyzkinosport.top and travelsreview.wo. So, enable email and web filters, limit the use of macros, and browse carefully if you want to stay safe.

4. Melissa
Here comes yet another harmful virus that sneaks into your computer via a Word document. The doc file entices you by giving the impression that it contains passwords for a few blocked websites.
Your computer becomes infected as soon as you open it. It does not stop here; through your email list, it spreads to other computers after infecting yours. Image Source: Panda Security
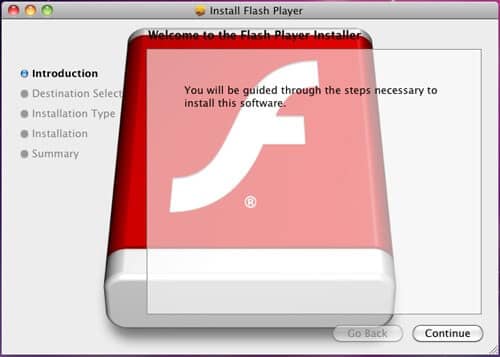
5. Flashback
This Trojan hacks into your PC under the false appearance of a flash installation. It was first discovered in 2011. To propagate itself, it makes use of poorly written JavaScript codes. Once your computer is infected, the virus uses these codes to spread to other computers.
Furthermore, this Trojan has infected roughly 6,00,000 Macs in a short period of time, and even the so-called invulnerable Mac has not been spared from this virus.
6. Zeus
The Trojan was created by true criminals with the intention of forcing your computer to carry out unlawful activities. This most recent virus invades your computer and steals your private information, including passwords to your email, banking, and social media accounts.
After that, it makes use of it to commit crimes like form grabbing and keylogging.
Also know: Best Free Security Software for Windows PC in 2023
7. RaaS
RaaS is an acronym that stands for “Ransomware as a Service.” The hacking industry is seeing a rise in this trend. Here, the hackers hire additional attackers to complete the task because they lack the knowledge to carry out attacks in a sophisticated manner.
Everybody in the world should be concerned about the speed at which RaaS is spreading.
8. Mydoom
The second-fastest-moving virus after the ILOVEYOU virus is Mydoom, which was first discovered in 2009. “Andy, I’m just doing my job, nothing personal, sorry” is the subject of an email that spreads the virus. Once it has infected one PC, it spreads to additional PCs by way of the user’s email address book.
This is one of the recently discovered dangerous computer viruses that were widely disseminated and is said to have cost $38 billion in damages.

9. Fantom ransomware
Fantom is a ransomware-like virus that encrypts files while pretending to be a Windows update. This is unusual because most ransomware silently encrypts files without any visible activity. Fantom appends the “.locked4”, “.fantom,” or “.locked” extensions to the names of encrypted files during encryption. For instance, the name “sample.jpg” of an encrypted image file is changed to “sample.jpg.fantom.”
A “DECRYPT_YOUR_FILES.html” file is created by Fantom and placed on the desktop and in each folder containing encrypted files after encryption is successful. Fantom also modifies the desktop wallpaper after encryption is complete.
10. Mindware
A new ransomware gang called Mindware started to show up in the cybercrime landscape in the middle of last month. MalwareHunterTeam, a cybersecurity researcher, has denounced it. Their malicious code, most likely SFile2, is a member of the SFile family.
The expert claims that it is currently impossible to determine whether this gang is brand-new or a reincarnation of one that already existed. It is certain that the double extortion scheme is exploited in order to put more pressure on victims and compel them to pay the ransom.
Frequently Asked Questions
Q1. What are the different types of computer viruses?
The virus threat may appear in various forms. The most popular ones are listed below.
- Malware: All software that can inadvertently or intentionally damage your computer is referred to as malware. They might steal your sensitive information and use it fraudulently. Malware can take the form of viruses, worms, Trojan horses, adware, spyware, and ransomware, to name a few.
- Ransomware: This kind of malware holds your data captive by encrypting it and requesting payment in exchange. In recent years, there have been numerous instances of large corporations and governments falling victim to ransomware attacks.
- Trojans: This kind of malware enters your computer through an email attachment that appears to be completely legitimate. They typically arrive in the form of an email attachment that offers protection against a fictitious virus threat. As soon as you open that attachment, Tojans attack your computer and steal any data you have on it.
Q2. Which is more dangerous, a worm or a virus?
Worms have the ability to reproduce. As a result, a worm infection spreads faster and gets into every crevice of the computer. However, it does not imply that you should disregard viruses. They are also equally harmful.
Q3. What is the most harmful computer virus in the world?
All computer viruses are dangerous and cause harm. But among all viruses ever made, ILOVEYOU was among the most harmful ones. This dangerous virus caused damage worth more than $10 million throughout the world.
Q4. Does resetting the computer remove viruses?
The virus’s hiding place is removed by factory resets. As a result, it is one of the best methods for eliminating both recent and old computer viruses. But it also erases all of the data on your computer in addition to clearing your PC of virus threats. So, before performing a factory reset, make sure you have a data backup.
Q5. What are the signs of a virus infection on the computer?
There is a good chance that your computer may be infected with a new computer virus if you experience any of the symptoms listed below.
- Frequent error notifications.
- Unanticipated shutdowns.
- Inexplicably long startup/shutdown times are experienced by PCs.
- Unknowledgeable toolbars.
- Unauthorized changes to the homepage.
- The battery drains quickly.
Latest Computer Viruses 2023
The most recent computer viruses as of 2023 are listed above, along with tips on how to avoid getting infected. It’s not the end of the list of viruses. Every day, a new, terrifying virus makes its way into the world of computers. If this worries you, get a strong antivirus program like Malwarebytes that can combat these viruses and protect your system. Last but not least, before you go, remember to subscribe to our newsletter for more fascinating tech news.

